The Latest
-
Alert: Exposed JDWP Interfaces Lead to Crypto Mining, Hpingbot Targets SSH for DDoS
-
Taiwan NSB Alerts Public on Data Risks from TikTok, Weibo, and RedNote Over China Ties
-
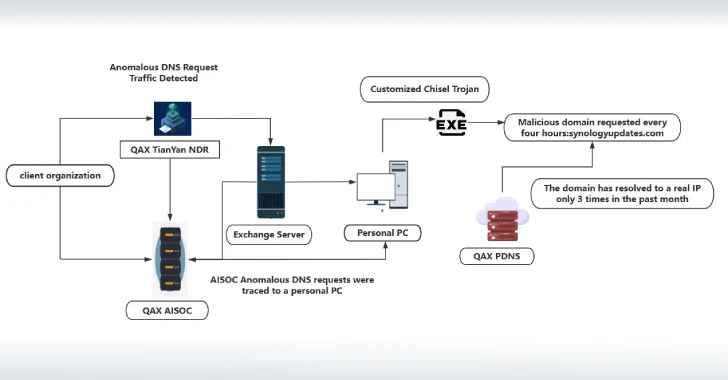
NightEagle APT Exploits Microsoft Exchange Flaw to Target China's Military and Tech Sectors
-
Critical Sudo Vulnerabilities Let Local Users Gain Root Access on Linux, Impacting Major Distros