The Latest
-
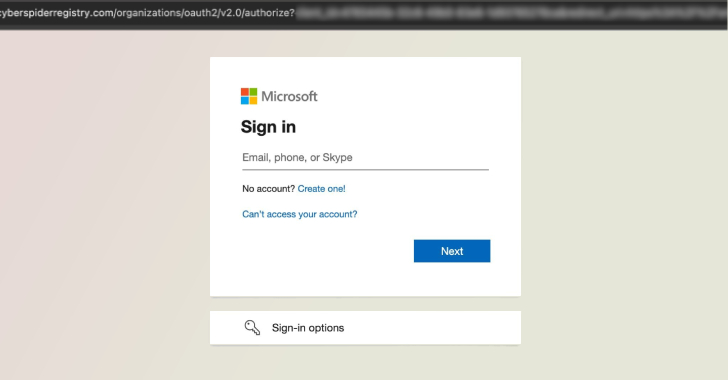
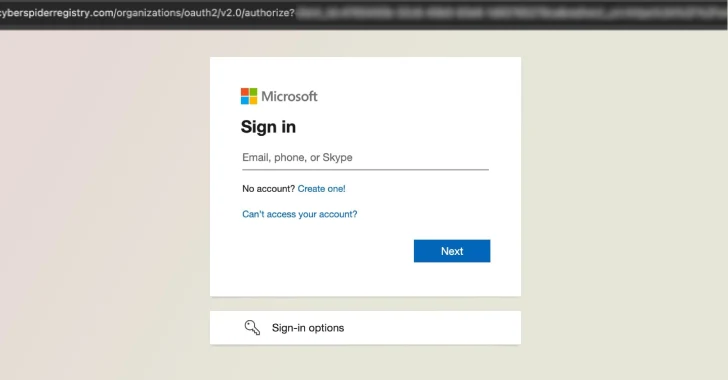
RaccoonO365 Phishing Network Dismantled as Microsoft, Cloudflare Take Down 338 Domains
-
DOJ Resentences BreachForums Founder to 3 Years for Cybercrime and Possession of CSAM
-
RaccoonO365 Phishing Network Shut Down After Microsoft and Cloudflare Disrupt 338 Domains
-
Self-Replicating Worm Hits 180+ npm Packages to Steal Credentials in Latest Supply Chain Attack