The Latest
-
From Backup to Cyber Resilience: Why IT Leaders Must Rethink Backup in the Age of Ransomware
-
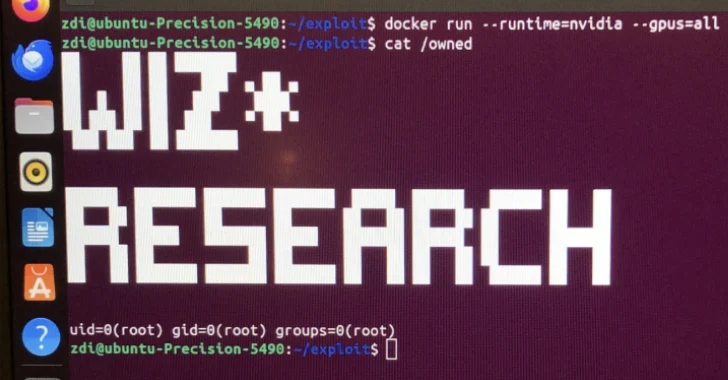
Critical NVIDIA Container Toolkit Flaw Allows Privilege Escalation on AI Cloud Services
-
Google Sues 25 Chinese Entities Over BADBOX 2.0 Botnet Affecting 10M Android Devices
-
Hackers Use GitHub Repositories to Host Amadey Malware and Data Stealers, Bypassing Filters