The Latest
-
Critical Unpatched SharePoint Zero-Day Actively Exploited, Breaches 75+ Global Organizations
-
Hackers Exploit Critical CrushFTP Flaw to Gain Admin Access on Unpatched Servers
-
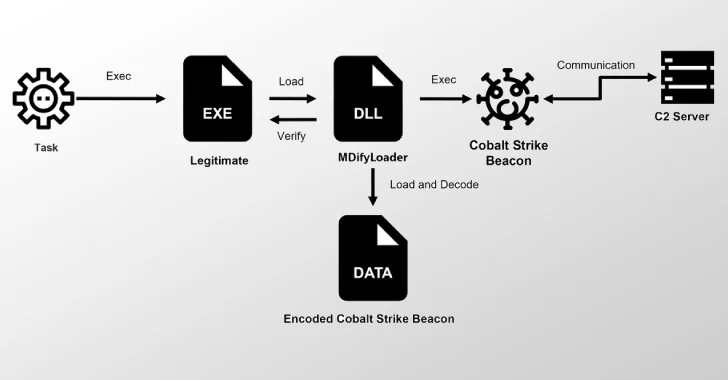
Ivanti Zero-Days Exploited to Drop MDifyLoader and Launch In-Memory Cobalt Strike Attacks
-
UNG0002 Group Hits China, Hong Kong, Pakistan Using LNK Files and RATs in Twin Campaigns