The Latest
-
The 5 Golden Rules of Safe AI Adoption
-
Blind Eagle’s Five Clusters Target Colombia Using RATs, Phishing Lures, and Dynamic DNS Infra
-
Salesloft OAuth Breach via Drift AI Chat Agent Exposes Salesforce Customer Data
-
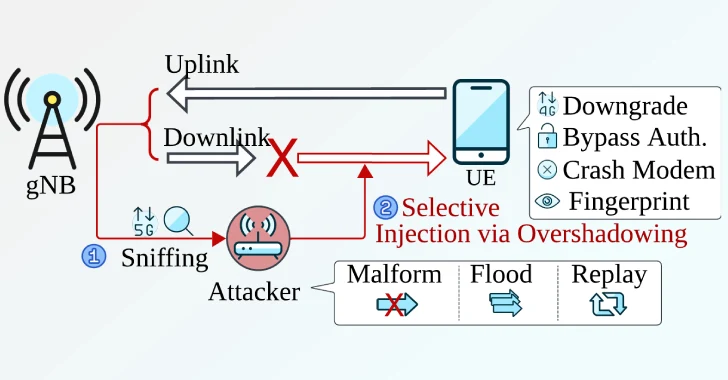
New Sni5Gect Attack Crashes Phones and Downgrades 5G to 4G without Rogue Base Station