The Latest
-
Transparent Tribe Targets Indian Govt With Weaponized Desktop Shortcuts via Phishing
-
Malicious Go Module Poses as SSH Brute-Force Tool, Steals Credentials via Telegram Bot
-
GeoServer Exploits, PolarEdge, and Gayfemboy Push Cybercrime Beyond Traditional Botnets
-
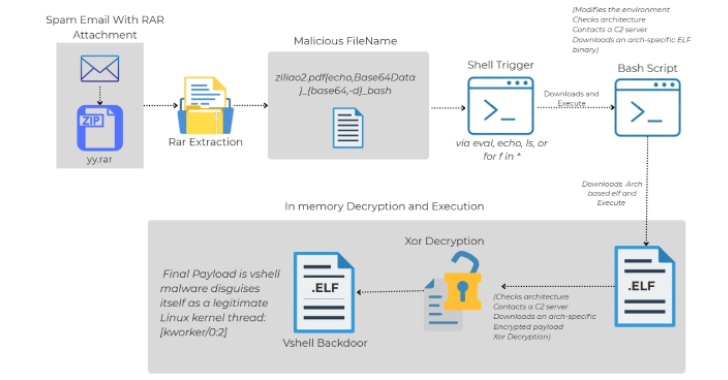
Linux Malware Delivered via Malicious RAR Filenames Evades Antivirus Detection