The Latest
-
UNC6148 Backdoors Fully-Patched SonicWall SMA 100 Series Devices with OVERSTEP Rootkit
-
AI Agents Act Like Employees With Root Access—Here's How to Regain Control
-
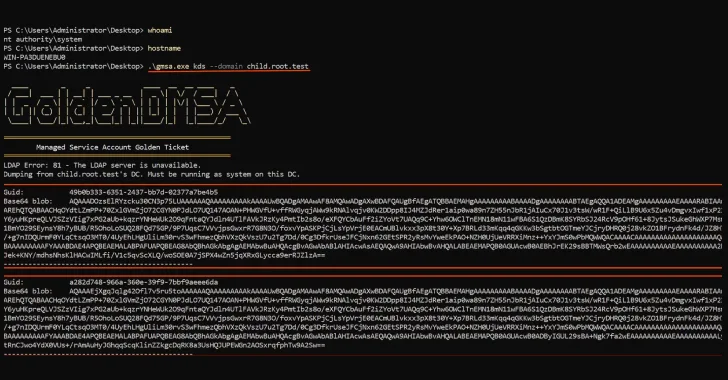
Critical Golden dMSA Attack in Windows Server 2025 Enables Cross-Domain Attacks and Persistent Access
-
Deepfakes. Fake Recruiters. Cloned CFOs — Learn How to Stop AI-Driven Attacks in Real Time