The Latest
-
3 SOC Challenges You Need to Solve Before 2026
-
CISA Warns of Active Spyware Campaigns Hijacking High-Value Signal and WhatsApp Users
-
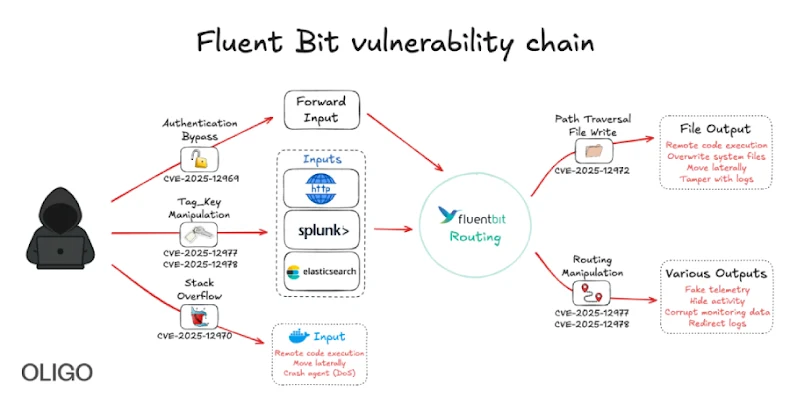
New Fluent Bit Flaws Expose Cloud to RCE and Stealthy Infrastructure Intrusions
-
⚡ Weekly Recap: Fortinet Exploit, Chrome 0-Day, BadIIS Malware, Record DDoS, SaaS Breach & More