The Latest
-
Why Unmonitored JavaScript Is Your Biggest Holiday Security Risk
-
Microsoft Locks Down IE Mode After Hackers Turned Legacy Feature Into Backdoor
-
Researchers Warn RondoDox Botnet is Weaponizing Over 50 Flaws Across 30+ Vendors
-
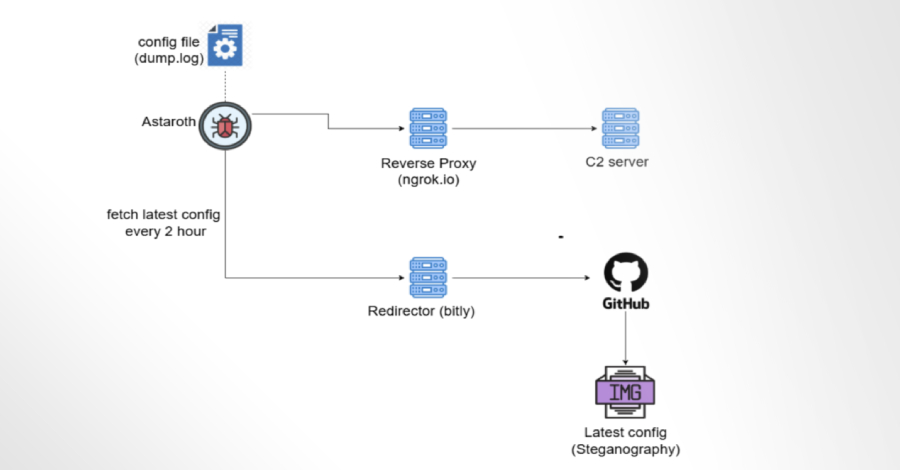
Astaroth Banking Trojan Abuses GitHub to Remain Operational After Takedowns