The Latest
-
Critical Mitel Flaw Lets Hackers Bypass Login, Gain Full Access to MiVoice MX-ONE Systems
-
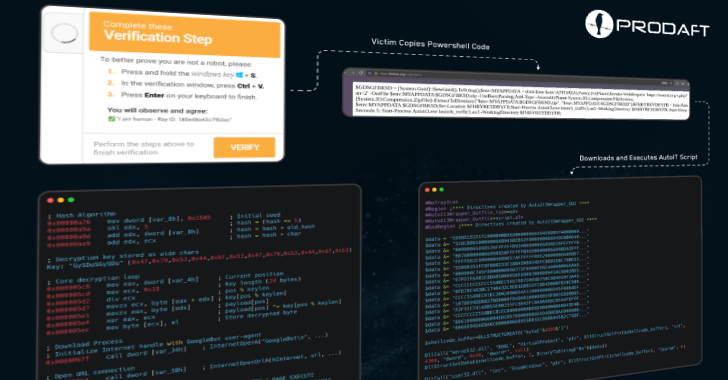
CastleLoader Malware Infects 469 Devices Using Fake GitHub Repos and ClickFix Phishing
-
Sophos and SonicWall Patch Critical RCE Flaws Affecting Firewalls and SMA 100 Devices
-
China-Based APTs Deploy Fake Dalai Lama Apps to Spy on Tibetan Community