The Latest
-
Hackers Actively Exploiting 7-Zip Symbolic Link–Based RCE Vulnerability (CVE-2025-11001)
-
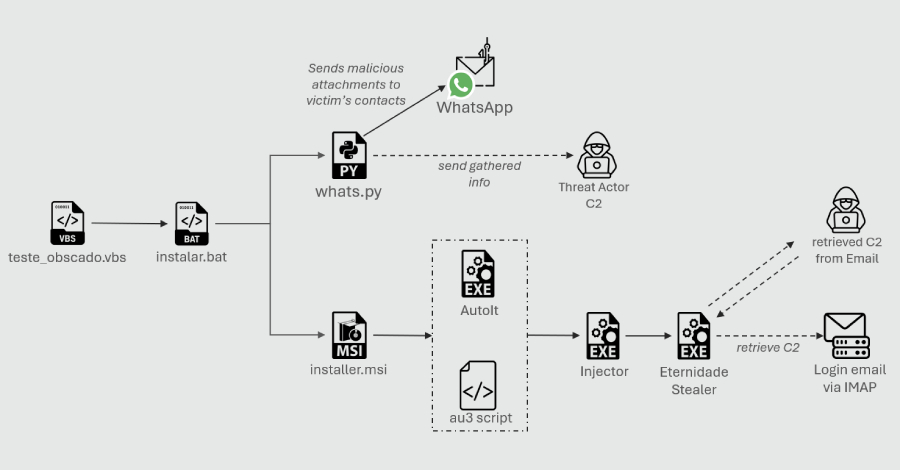
Python-Based WhatsApp Worm Spreads Eternidade Stealer Across Brazilian Devices
-
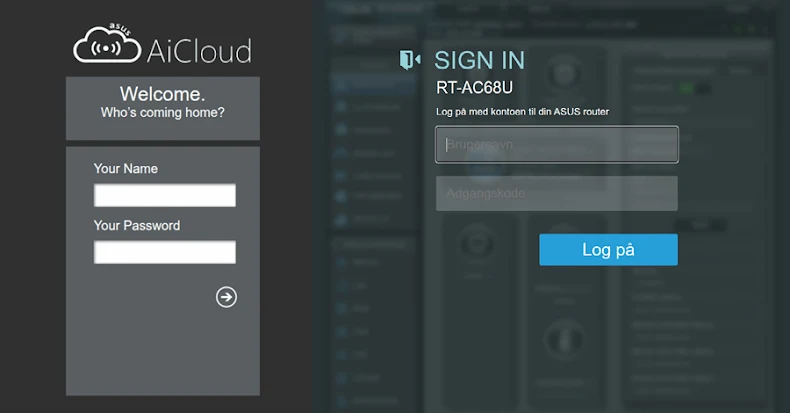
WrtHug Exploits Six ASUS WRT Flaws to Hijack Tens of Thousands of EoL Routers Worldwide
-
Application Containment: How to Use Ringfencing to Prevent the Weaponization of Trusted Software