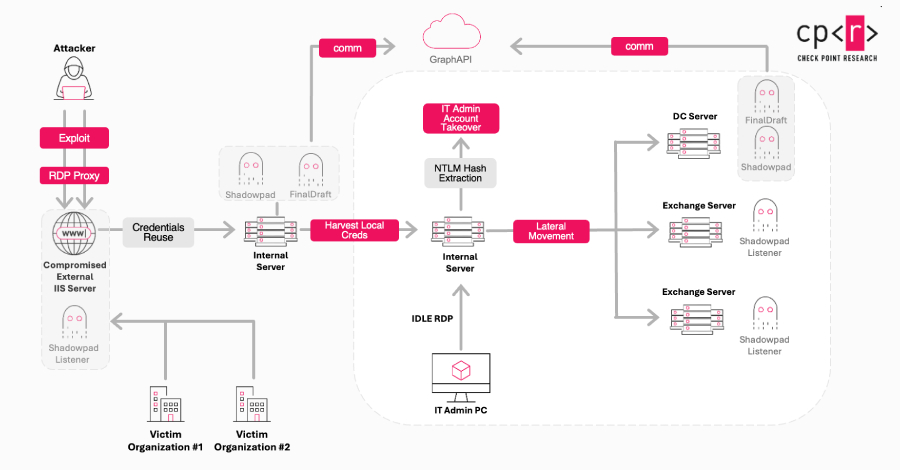
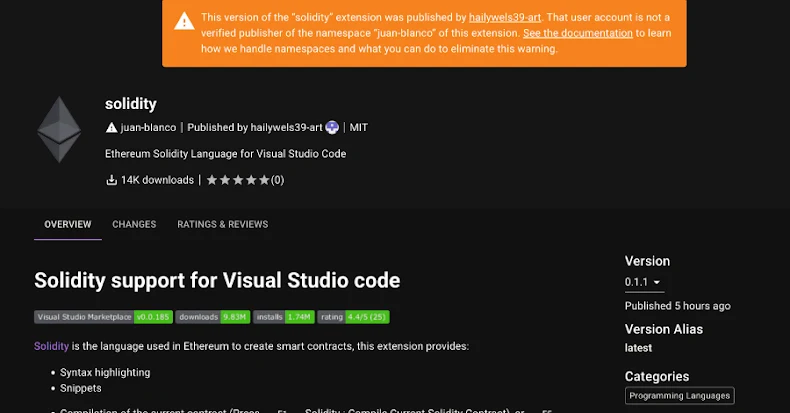
The Latest
-
Google’s AI ‘Big Sleep’ Finds 5 New Vulnerabilities in Apple’s Safari WebKit
-
Microsoft Detects "SesameOp" Backdoor Using OpenAI's API as a Stealth Command Channel
-
Malicious VSX Extension "SleepyDuck" Uses Ethereum to Keep Its Command Server Alive
-
Cybercriminals Exploit Remote Monitoring Tools to Infiltrate Logistics and Freight Networks