The Latest
-
6 Lessons Learned: Focusing Security Where Business Value Lives
-
WinRAR Zero-Day Under Active Exploitation – Update to Latest Version Immediately
-
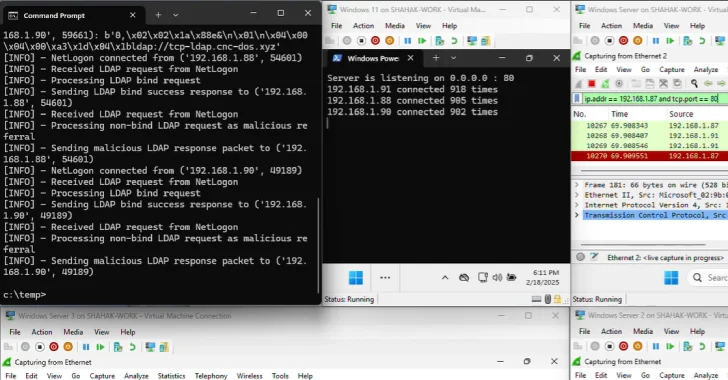
New Win-DDoS Flaws Let Attackers Turn Public Domain Controllers into DDoS Botnet via RPC, LDAP
-
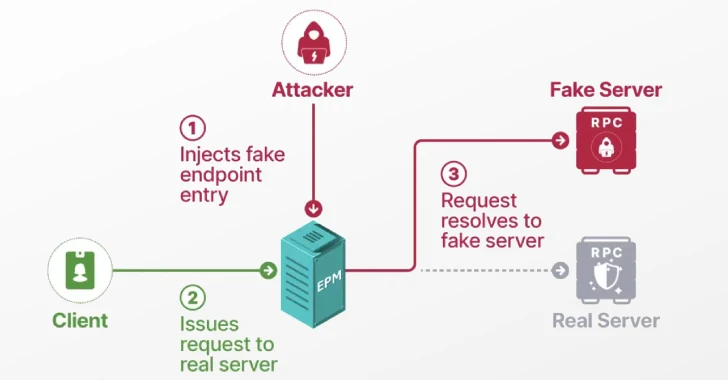
Researchers Detail Windows EPM Poisoning Exploit Chain Leading to Domain Privilege Escalation