The Latest
-
Hackers Exploit Apache HTTP Server Flaw to Deploy Linuxsys Cryptocurrency Miner
-
CTEM vs ASM vs Vulnerability Management: What Security Leaders Need to Know in 2025
-
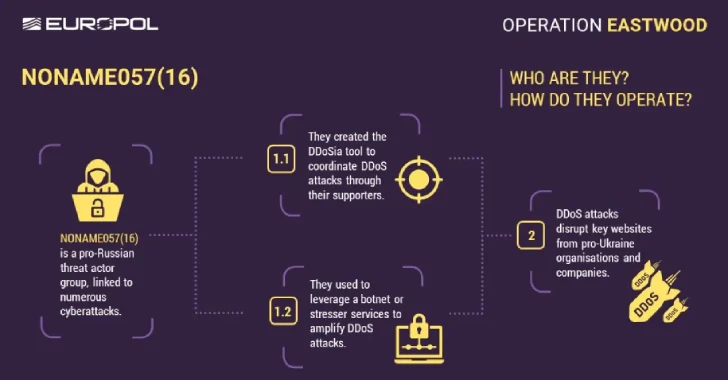
Europol Disrupts NoName057(16) Hacktivist Group Linked to DDoS Attacks Against Ukraine
-
Chinese Hackers Target Taiwan's Semiconductor Sector with Cobalt Strike, Custom Backdoors