The Latest
-
State-Backed HazyBeacon Malware Uses AWS Lambda to Steal Data from SE Asian Governments
-
North Korean Hackers Flood npm Registry with XORIndex Malware in Ongoing Attack Campaign
-
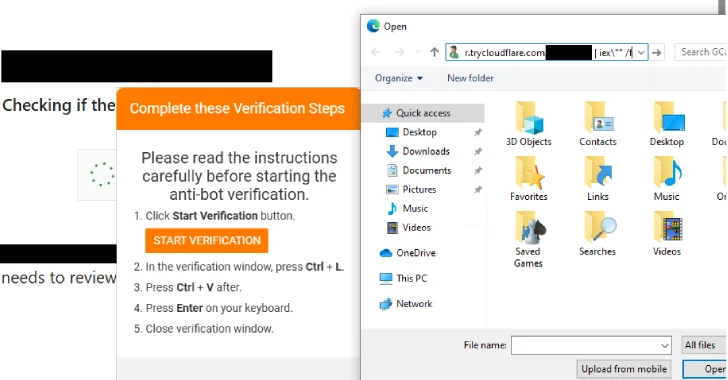
New PHP-Based Interlock RAT Variant Uses FileFix Delivery Mechanism to Target Multiple Industries
-
The Unusual Suspect: Git Repos