The Latest
-
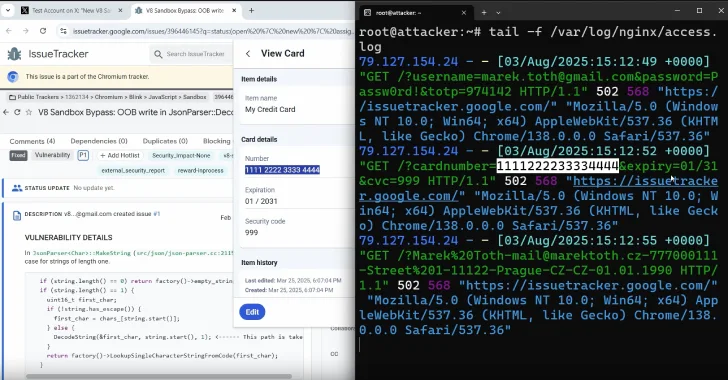
DOM-Based Extension Clickjacking Exposes Popular Password Managers to Credential and Data Theft
-
Experts Find AI Browsers Can Be Tricked by PromptFix Exploit to Run Malicious Hidden Prompts
-
🕵️ Webinar: Discover and Control Shadow AI Agents in Your Enterprise Before Hackers Do
-
From Impact to Action: Turning BIA Insights Into Resilient Recovery