The Latest
-
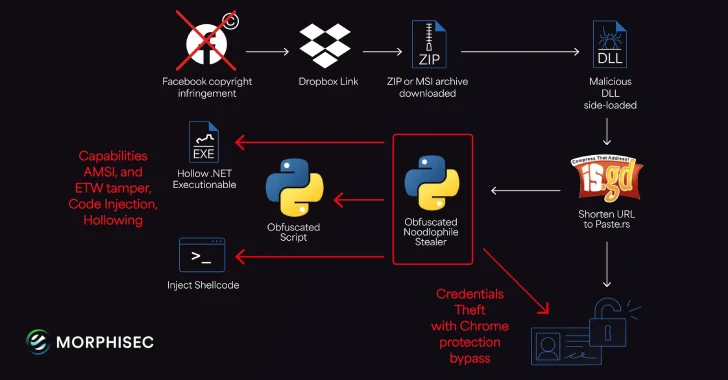
Noodlophile Malware Campaign Expands Global Reach with Copyright Phishing Lures
-
Microsoft Windows Vulnerability Exploited to Deploy PipeMagic RansomExx Malware
-
⚡ Weekly Recap: NFC Fraud, Curly COMrades, N-able Exploits, Docker Backdoors & More
-
Malicious PyPI and npm Packages Discovered Exploiting Dependencies in Supply Chain Attacks