The Latest
-
Critical CVE-2025-5086 in DELMIA Apriso Actively Exploited, CISA Issues Warning
-
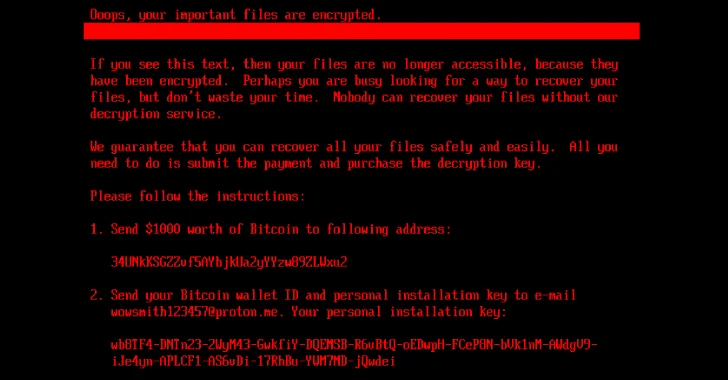
New HybridPetya Ransomware Bypasses UEFI Secure Boot With CVE-2024-7344 Exploit
-
Cloud-Native Security in 2025: Why Runtime Visibility Must Take Center Stage
-
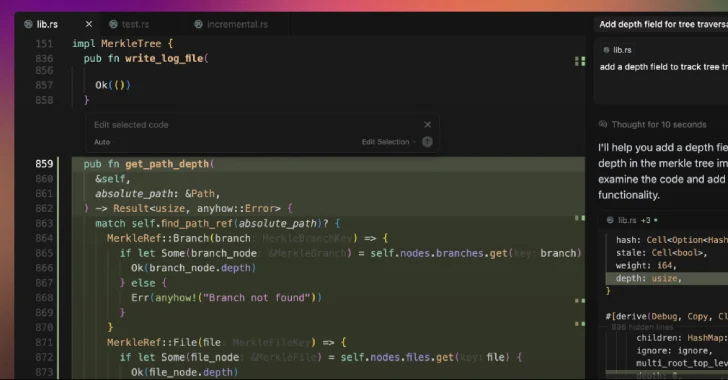
Cursor AI Code Editor Flaw Enables Silent Code Execution via Malicious Repositories