The Latest
-
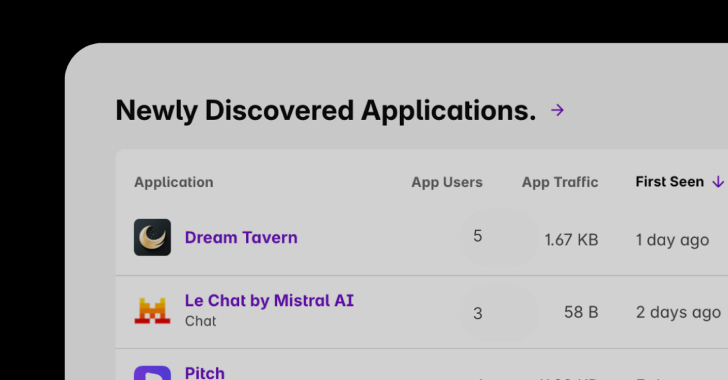
Shadow AI Discovery: A Critical Part of Enterprise AI Governance
-
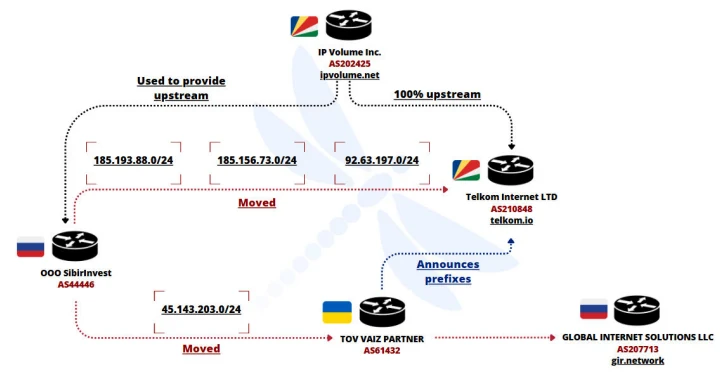
Ukrainian Network FDN3 Launches Massive Brute-Force Attacks on SSL VPN and RDP Devices
-
Silver Fox Exploits Microsoft-Signed WatchDog Driver to Deploy ValleyRAT Malware
-
Malicious npm Package nodejs-smtp Mimics Nodemailer, Targets Atomic and Exodus Wallets