The Latest
-
Stealit Malware Abuses Node.js Single Executable Feature via Game and VPN Installers
-
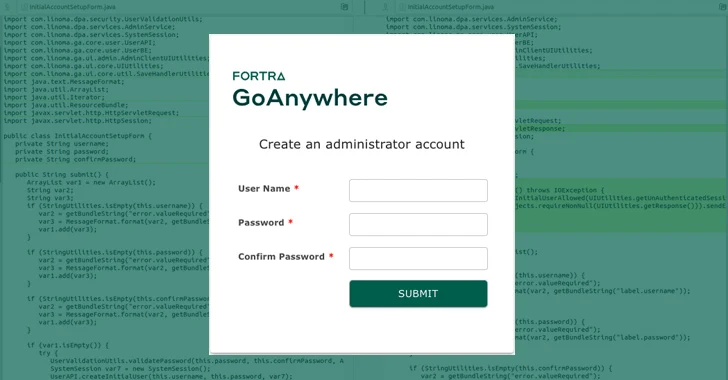
From Detection to Patch: Fortra Reveals Full Timeline of CVE-2025-10035 Exploitation
-
175 Malicious npm Packages with 26,000 Downloads Used in Credential Phishing Campaign
-
The AI SOC Stack of 2026: What Sets Top-Tier Platforms Apart?