The Latest
-
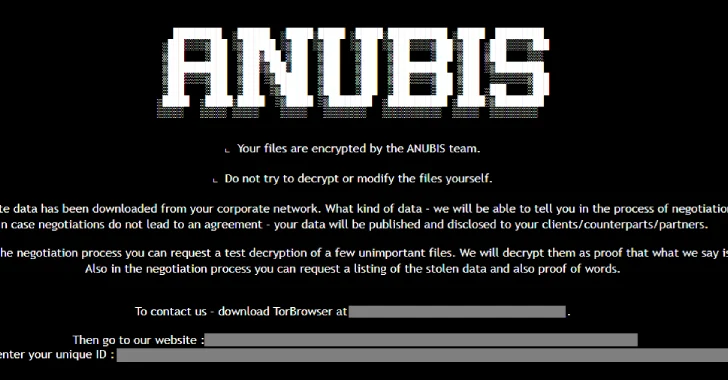
Anubis Ransomware Encrypts and Wipes Files, Making Recovery Impossible Even After Payment
-
Playbook: Transforming Your Cybersecurity Practice Into An MRR Machine
-
⚡ Weekly Recap: iPhone Spyware, Microsoft 0-Day, TokenBreak Hack, AI Data Leaks and More
-
Malicious PyPI Package Masquerades as Chimera Module to Steal AWS, CI/CD, and macOS Data