The exploitation of a recently disclosed critical security flaw in Motex Lanscope Endpoint Manager has been attributed to a cyber espionage group known as Tick.
The vulnerability, tracked as CVE-2025-61932 (CVSS score: 9.3), allows remote attackers to execute arbitrary commands with SYSTEM privileges on on-premise versions of the program. JPCERT/CC, in an alert issued this month, said that it has confirmed reports of active abuse of the security defect to drop a backdoor on compromised systems.
Tick, also known as Bronze Butler, Daserf, REDBALDKNIGHT, Stalker Panda, Stalker Taurus, and Swirl Typhoon (formerly Tellurium), is a suspected Chinese cyber espionage actor known for its extensive targeting of East Asia, specifically Japan. It’s assessed to be active since at least 2006.
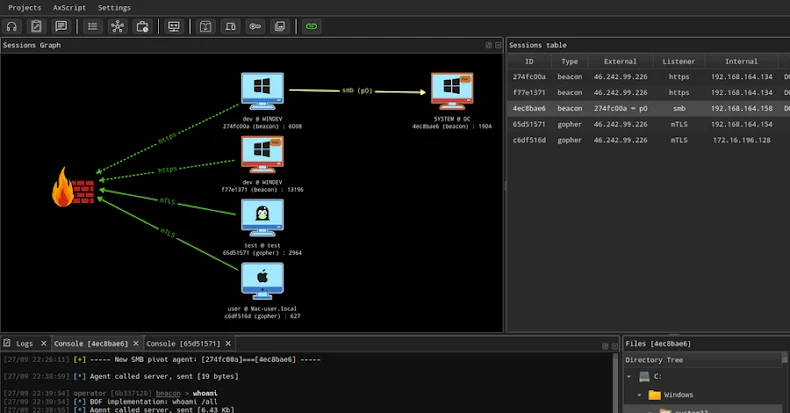
The sophisticated campaign, observed by Sophos, involved the exploitation of CVE-2025-61932 to deliver a known backdoor referred to as Gokcpdoor that can establish a proxy connection with a remote server and act as a backdoor to execute malicious commands on the compromised host.
“The 2025 variant discontinued support for the KCP protocol and added multiplexing communication using a third-party library [smux] for its C2 [command-and-control] communication,” the Sophos Counter Threat Unit (CTU) said in a Thursday report.
The cybersecurity company said it detected two different types of Gokcpdoor serving distinct use-cases –
- A server type that listens for incoming client connections to enable remote access
- A client type that initiates connections to hard-coded C2 servers with the goal of setting up a covert communication channel
The attack is also characterized by the deployment of the Havoc post-exploitation framework on select systems, with the infection chains relying on DLL side-loading to launch a DLL loader named OAED Loader to inject the payloads.
Some of the other tools utilized in the attack to facilitate lateral movement and data exfiltration include goddi, an open-source Active Directory information dumping tool; Remote Desktop, for remote access through a backdoor tunnel; and 7-Zip.
The threat actors have also been found to access cloud services such as io, LimeWire, and Piping Server via the web browser during remote desktop sessions in an effort to exfiltrate the harvested data.
This is not the first time Tick has been observed leveraging a zero-day flaw in its attack campaigns. In October 2017, Sophos-owned Secureworks detailed the hacking group’s exploitation of a then-unpatched remote code execution vulnerability (CVE-2016-7836) in SKYSEA Client View, a Japanese IT asset management software, to compromise machines and steal data.
“Organizations upgrade vulnerable LANSCOPE servers as appropriate in their environments, “Sophos TRU said. “Organizations should also review internet-facing LANSCOPE servers that have the LANSCOPE client program (MR) or detection agent (DA) installed to determine if there is a business need for them to be publicly exposed.”
Source: thehackernews.com…