Enterprises today are expected to have at least 6-8 detection tools, as detection is considered a standard investment and the first line of defense. Yet security leaders struggle to justify dedicating resources further down the alert lifecycle to their superiors.
As a result, most organizations’ security investments are asymmetrical, robust detection tools paired with an under-resourced SOC, their last line of defense.
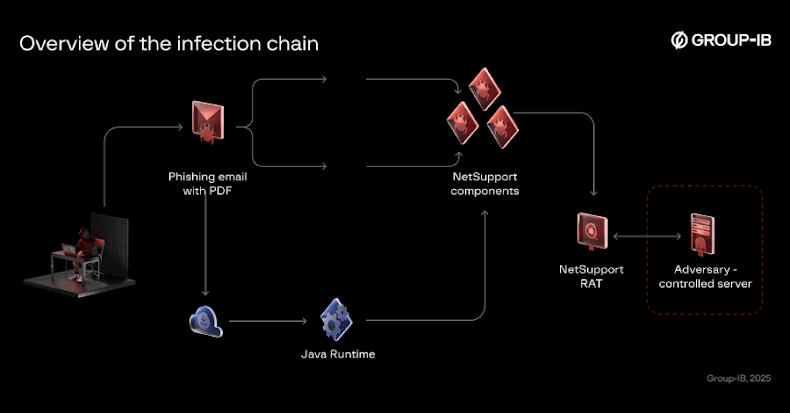
A recent case study demonstrates how companies with a standardized SOC prevented a sophisticated phishing attack that bypassed leading email security tools. In this case study, a cross-company phishing campaign targeted C-suite executives at multiple enterprises. Eight different email security tools across these organizations failed to detect the attack, and phishing emails reached executive inboxes. However, each organization’s SOC team detected the attack immediately after employees reported the suspicious emails.
Why did all eight detection tools identically fail where the SOC succeeded?
What all these organizations have in common is a balanced investment across the alert lifecycle, which doesn’t neglect their SOC.
This article examines how investing in the SOC is indispensable for organizations that have already allocated significant resources to detection tools. Additionally, a balanced SOC investment is crucial for maximizing the value of their existing detection investments.
Detection tools and the SOC operate in parallel universes
Understanding this fundamental disconnect explains how security gaps arise:
Detection tools operate in milliseconds. They must make instant decisions on millions of signals every day. They have no time for nuance; speed is essential. Without it, networks would come to a halt, as every email, file, and connection request would be held up for analysis.
Detection tools zoom in. They are the first to identify and isolate potential threats, but they lack an understanding of the bigger picture. Meanwhile, SOC teams operate with a 30K feet view. When alerts reach analysts, they have something detection tools lack: time and context.
Consequently, the SOC tackles alerts from a different perspective:
- They can analyze behavioral patterns, such as why an executive suddenly logs in from a datacenter IP address when they usually work from London.
- They can stitch data across tools. They can view a clean reputation email domain along with subsequent authentication attempts and user reports.
- They can identify patterns that only make sense when seen together, such as exclusive targeting of finance executives combined with timing that aligns with payroll cycles.
Three critical risks of an underfunded SOC
First, it can make it more difficult for executive leadership to identify the root of the problem. CISOs and budget holders in organizations that deploy various detection tools often assume their investments will keep them safe. Meanwhile, the SOC experiences this differently, overwhelmed by noise and lacking the resources to properly investigate real threats. Because detection spending is obvious, while SOC struggles happen behind closed doors, security leaders find it challenging to demonstrate the need for additional investment in their SOC.
Second, the asymmetry overwhelms the last line of defense. Significant investments in multiple detection tools produce thousands of alerts that flood the SOC every day. With underfunded SOCs, analysts become goalies facing hundreds of shots at once, forced to make split-second decisions under immense pressure.
Third, it undermines the ability to identify nuanced threats. When the SOC is overwhelmed by alerts, the capacity for detailed investigative work is lost. The threats that escape detection are the ones that detection tools would never catch in the first place.
From temporary fixes to sustainable SOC operations
When detection tools generate hundreds of alerts daily, adding a few more SOC analysts is as effective as trying to save a sinking ship with a bucket. The traditional alternative has been outsourcing to MSSPs or MDRs and assigning external teams to handle overflow.
But for many, the trade-offs are still too much: high ongoing costs, shallow analyst investigations that are unfamiliar with your environment, delays in coordination, and broken communication. Outsourcing doesn’t fix the imbalance; it just shifts the burden onto someone else’s plate.
Today, AI SOC platforms are becoming the preferred choice for organizations with lean SOC teams looking for an efficient, cost-effective, and scalable solution. AI SOC platforms operate at the investigation layer where contextual reasoning happens, automate alert triage, and surface only high-fidelity incidents after assigning them context.
With the help of AI SOC, analysts save hundreds of hours each month, as false-positive rates often drop by more than 90%. This automated coverage enables small internal teams to provide 24/7 coverage without additional staffing or outsourcing. The companies featured in this case study invested in this approach through Radiant Security, an agentic AI SOC platform.
2 ways SOC investment pays off, now and later
- SOC investments make the cost of detection tools worthwhile. Your detection tools are only as effective as your ability to investigate their alerts. When 40% of alerts go uninvestigated, you’re not getting the full value of every detection tool you own. Without sufficient SOC capacity, you’re paying for detection capabilities that you can’t fully utilize.
- The last line’s unique perspective will become increasingly critical. SOC will become increasingly essential as detection tools fail more often. As attacks grow more sophisticated, detection will need more context. The SOC’s perspective will mean only they can connect these dots and see the entire picture.
3 questions to guide your next security budget
- Is your security investment symmetric? Begin by assessing your resource allocation for imbalance. The first indication of asymmetrical security is having more alerts than your SOC can handle. If your analysts are overwhelmed by alerts, it means your frontline is exceeding your backline.
- Is your SOC a qualified safety net? Every SOC leader must ask, if detection fails, is the SOC prepared to catch what gets through? Many organizations never ask this because they don’t see detection as the SOC’s responsibility. But when detection tools fail, responsibilities shift.
- Are you underutilizing existing tools? Many organizations find that their detection tools produce valuable signals that no one has time to investigate. Asymmetry means lacking the ability to act on what you already possess.
Key takeaways from Radiant Security
Most security teams have the opportunity to allocate resources to maximize ROI from their current detection investments, support future growth, and enhance protection. Organizations that invest in detection tools but neglect their SOC create blind spots and burnout.
Radiant Security, the agentic AI SOC platform highlighted in the case study, shows success through balanced security investment. Radiant works at the SOC investigation layer, automatically triaging every alert, cutting false positives by about 90%, and analyzing threats at machine speed, like a top analyst. With over 100 integrations with existing security tools and one-click response features, Radiant helps lean security teams investigate any alert, known or unknown, without needing impossible headcount increases. Radiant security makes enterprise-grade SOC capabilities available to organizations of any size.
Found this article interesting?
This article is a contributed piece from one of our valued partners. Follow us on
Google News,
Twitter and
LinkedIn to read more exclusive content we post.