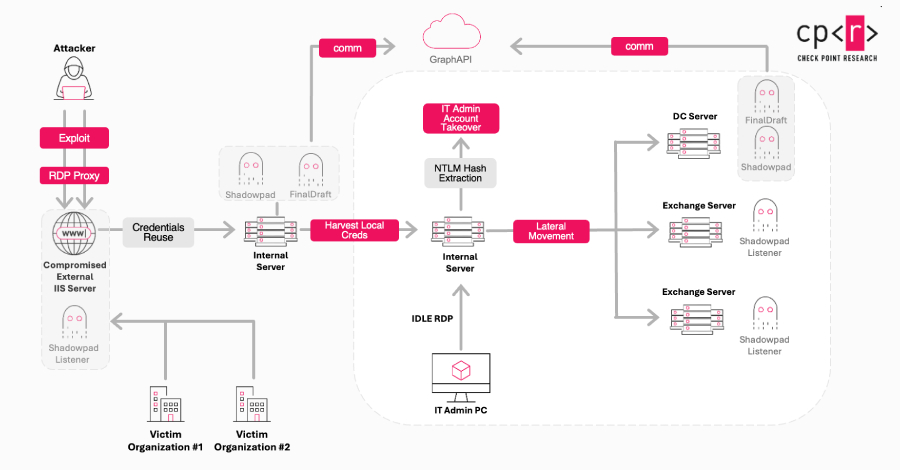
Modern security teams often feel like they’re driving through fog with failing headlights. Threats accelerate, alerts multiply, and SOCs struggle to understand which dangers matter right now for their business. Breaking out of reactive defense is no longer optional. It’s the difference between preventing incidents and cleaning up after them.
Below is the path from reactive firefighting to a proactive, context-rich SOC that actually sees what’s coming.
When the SOC Only Sees in the Rear-View Mirror
Many SOCs still rely on a backward-facing workflow. Analysts wait for an alert, investigate it, escalate, and eventually respond. This pattern is understandable: the job is noisy, the tooling is complex, and alert fatigue bends even the toughest teams into reactive mode.
But a reactive posture hides several structural problems:
- No visibility into what threat actors are preparing.
- Limited ability to anticipate campaigns targeting the organization’s sector.
- Inability to adjust defenses before an attack hits.
- Overreliance on signatures that reflect yesterday’s activity.
The result is a SOC that constantly catches up but rarely gets ahead.
The Cost of Waiting for the Alarm to Ring
Reactive SOCs pay in time, money, and risk.
- Longer investigations. Analysts must research every suspicious object from scratch because they lack a broader context.
- Wasted resources. Without visibility into which threats are relevant to their vertical and geography, teams chase false positives instead of focusing on real dangers.
- Higher breach likelihood. Threat actors often reuse infrastructure and target specific industries. Seeing these patterns late gives attackers the advantage.
A proactive SOC flips this script by reducing uncertainty. It knows which threats are circulating in its environment, what campaigns are active, and which alerts deserve immediate escalation.
Threat Intelligence: The Engine of Proactive Security
Threat intelligence fills the gaps left by reactive operations. It provides a stream of evidence about what attackers are doing right now and how their tools evolve.
ANY.RUN’s Threat Intelligence Lookup serves as a tactical magnifying glass for SOCs. It converts raw threat data into an operational asset.
 |
| TI Lookup: investigate threats and indicators, click search bar to select parameters |
Analysts can quickly:
- Enrich alerts with behavioral and infrastructure data;
- Identify malware families and campaigns with precision;
- Understand how a sample acts when detonated in a sandbox;
- Investigate artifacts, DNS, IPs, hashes, and relations in seconds.
For organizations that aim to build a more proactive stance, TI Lookup works as the starting point for faster triage, higher-confidence decisions, and a clearer understanding of threat relevance.
Turn intelligence into action, cut investigation time with instant threat context.
Contact ANY.RUN to integrate TI Lookup
ANY.RUN’s TI Feeds complement SOC workflows by supplying continuously updated indicators gathered from real malware executions. This ensures defenses adapt at the speed of threat evolution.
Focus on Threats that Actually Matter to Your Business
But context alone isn’t enough; teams need to interpret this intelligence for their specific business environment. Threats are not evenly distributed across the world. Each sector and region has its own constellation of malware families, campaigns, and criminal groups.
 |
| Companies from what industries and countries encounter Tycoon 2FA most often recently |
Threat Intelligence Lookup supports industry and geographic attribution of threats and indicators thus helping SOCs answer vital questions:
- Is this alert relevant to our company’s sector?
- Is this malware known to target companies in our country?
- Are we seeing the early movements of a campaign aimed at organizations like ours?
By mapping activity to both industry verticals and geographies, SOCs gain an immediate understanding of where a threat sits in their risk landscape. This reduces noise, speeds up triage, and lets teams focus on threats that truly demand action.
Focus your SOC on what truly matters.
See which threats target your sector today with TI Lookup.
Here is an example: a suspicious domain turns out to be linked to Lumma Stealer and ClickFix attacks targeting mostly telecom and hospitality businesses in the USA and Canada:
domainName:”benelui.click”
 |
| Industries and countries most targeted by threats the IOC is linked to |
Or suppose a CISO in German manufacturing company wants a baseline for sector risks:
industry:”Manufacturing” and submissionCountry:”DE”
 |
| TI Lookup summary on malware samples analyzed by German users and targeting manufacturing business |
This query surfaces top threats like Tycoon 2FA and EvilProxy plus highlights the interest of Storm-1747 APT group that operates Tycoon 2FA to the country’s production sector. This becomes an immediate priority list for detection engineering, threat hunting hypotheses, and security awareness training.
Analysts access sandbox sessions and real-world IOCs related to those threats. IOCs and TTPs instantly provided by TI Lookup fuel detection rules for the most relevant threats thus allowing to detect and mitigate incidents proactively, protecting businesses and their customers.
View a sandbox session of Lumma stealer sample analysis:
 |
| Sandbox analysis: see malware in action, view kill chain, gather IOCs |
Why the Threat Landscape Demands Better Visibility
Attackers’ infrastructure is changing fast and it’s no longer limited to one threat per campaign. We’re now seeing the emergence of hybrid threats, where multiple malware families are combined within a single operation. These blended attacks merge logic from different infrastructures, redirection layers, and credential-theft modules, making detection, tracking, and attribution significantly harder.
 |
| Hybrid attack with Salty and Tycoon detected inside ANY.RUN sandbox in just 35 seconds |
Recent investigations uncovered Tycoon 2FA and Salty working side by side in the same chain. One kit runs the initial lure and reverse proxy, while another takes over for session hijacking or credential capture. For many SOC teams, this combination breaks the existing defense strategies and detection rules, allowing attackers to slip past the security layer.
Tracking these changes across the broader threat landscape has become critical. Analysts must monitor behavior patterns and attack logic in real time, not just catalog kit variants. The faster teams can see these links forming, the faster they can respond to phishing campaigns built for adaptability.
Conclusion: A Clearer Horizon for Modern SOCs
Businesses can’t afford SOC blind spots anymore. Attackers specialize, campaigns localize, and malware evolves faster than signatures can keep up. Proactive defense requires context, clarity, and speed.
Threat Intelligence Lookup strengthened with industry and geo context and supported by fresh indicators from TI Feeds gives SOC leaders exactly that. Instead of reacting to alerts in the dark, decision makers gain a forward-looking view of the threats that really matter to their business.
Strengthen your security strategy with industry-specific visibility.
Contact ANY.RUN for actionable threat intelligence.
Found this article interesting?
This article is a contributed piece from one of our valued partners. Follow us on
Google News,
Twitter and
LinkedIn to read more exclusive content we post.