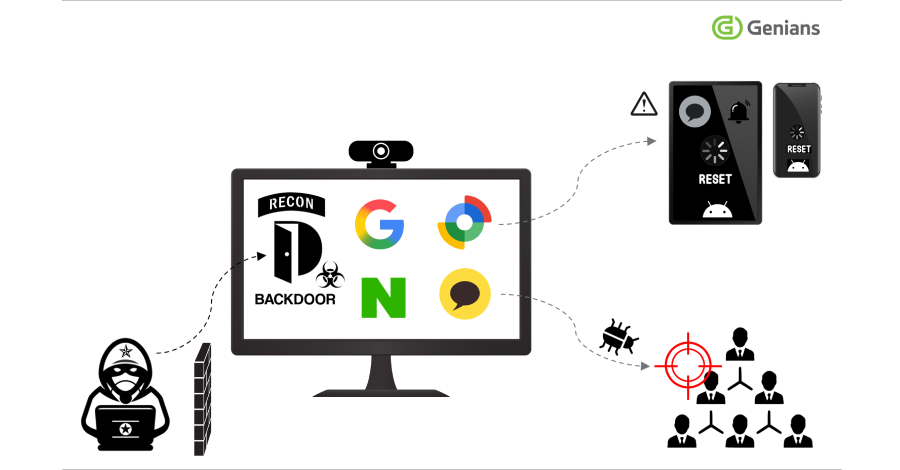
AI-enabled supply chain attacks jumped 156% last year. Discover why traditional defenses are failing and what CISOs must do now to protect their organizations.
Download the full CISO’s expert guide to AI Supply chain attacks here.
TL;DR
- AI-enabled supply chain attacks are exploding in scale and sophistication – Malicious package uploads to open-source repositories jumped 156% in the past year.
- AI-generated malware has game-changing characteristics – It’s polymorphic by default, context-aware, semantically camouflaged, and temporally evasive.
- Real attacks are already happening – From the 3CX breach affecting 600,000 companies to NullBulge attacks weaponizing Hugging Face and GitHub repositories.
- Detection times have dramatically increased – IBM’s 2025 report shows breaches take an average of 276 days to identify, with AI-assisted attacks potentially extending this window.
- Traditional security tools are struggling – Static analysis and signature-based detection fail against threats that actively adapt.
- New defensive strategies are emerging – Organizations are deploying AI-aware security to improve threat detection.
- Regulatory compliance is becoming mandatory – The EU AI Act imposes penalties of up to €35 million or 7% of global revenue for serious violations.
- Immediate action is critical – This isn’t about future-proofing but present-proofing.
The Evolution from Traditional Exploits to AI-Powered Infiltration
Remember when supply chain attacks meant stolen credentials and tampered updates? Those were simpler times. Today’s reality is far more interesting and infinitely more complex.
The software supply chain has become ground zero for a new breed of attack. Think of it like this: if traditional malware is a burglar picking your lock, AI-enabled malware is a shapeshifter that studies your security guards’ routines, learns their blind spots, and transforms into the cleaning crew.
Take the PyTorch incident. Attackers uploaded a malicious package called torchtriton to PyPI that masqueraded as a legitimate dependency. Within hours, it had infiltrated thousands of systems, exfiltrating sensitive data from machine learning environments. The kicker? This was still a “traditional” attack.
Fast forward to today, and we’re seeing something fundamentally different. Take a look at these three recent examples –
1. NullBulge Group – Hugging Face & GitHub Attacks (2024)
A threat actor called NullBulge conducted supply chain attacks by weaponizing code in open-source repositories on Hugging Face and GitHub, targeting AI tools and gaming software. The group compromised the ComfyUI_LLMVISION extension on GitHub and distributed malicious code through various AI platforms, using Python-based payloads that exfiltrated data via Discord webhooks and delivered customized LockBit ransomware.
2. Solana Web3.js Library Attack (December 2024)
On December 2, 2024, attackers compromised a publish-access account for the @solana/web3.js npm library through a phishing campaign. They published malicious versions 1.95.6 and 1.95.7 that contained backdoor code to steal private keys and drain cryptocurrency wallets, resulting in the theft of approximately $160,000–$190,000 worth of crypto assets during a five-hour window.
3. Wondershare RepairIt Vulnerabilities (September 2025)
The AI-powered image and video enhancement application Wondershare RepairIt exposed sensitive user data through hardcoded cloud credentials in its binary. This allowed potential attackers to modify AI models and software executables and launch supply chain attacks against customers by replacing legitimate AI models retrieved automatically by the application.
Download the CISO’s expert guide for full vendor listings and implementation steps.
The Rising Threat: AI Changes Everything
Let’s ground this in reality. The 3CX supply chain attack of 2023 compromised software used by 600,000 companies worldwide, from American Express to Mercedes-Benz. While not definitively AI-generated, it demonstrated the polymorphic characteristics we now associate with AI-assisted attacks: each payload was unique, making signature-based detection useless.
According to Sonatype’s data, malicious package uploads jumped 156% year-over-year. More concerning is the sophistication curve. MITRE’s recent analysis of PyPI malware campaigns found increasingly complex obfuscation patterns consistent with automated generation, though definitive AI attribution remains challenging.
Here’s what makes AI-generated malware genuinely different:
- Polymorphic by default: Like a virus that rewrites its own DNA, each instance is structurally unique while maintaining the same malicious purpose.
- Context-aware: Modern AI malware includes sandbox detection that would make a paranoid programmer proud. One recent sample waited until it detected Slack API calls and Git commits, signs of a real development environment, before activating.
- Semantically camouflaged: The malicious code doesn’t just hide; it masquerades as legitimate functionality. We’ve seen backdoors disguised as telemetry modules, complete with convincing documentation and even unit tests.
- Temporally evasive: Patience is a virtue, especially for malware. Some variants lie dormant for weeks or months, waiting for specific triggers or simply outlasting security audits.
Why Traditional Security Approaches Are Failing
Most organizations are bringing knives to a gunfight, and the guns are now AI-powered and can dodge bullets.
Consider the timeline of a typical breach. IBM’s Cost of a Data Breach Report 2025 found it takes organizations an average of 276 days to identify a breach and another 73 days to contain it. That’s nine months where attackers own your environment. With AI-generated variants that mutate daily, your signature-based antivirus is essentially playing whack-a-mole blindfolded.
AI isn’t just creating better malware, it’s revolutionizing the entire attack lifecycle:
- Fake Developer Personas: Researchers have documented “SockPuppet” attacks where AI-generated developer profiles contributed legitimate code for months before injecting backdoors. These personas had GitHub histories, Stack Overflow participation, and even maintained personal blogs – all generated by AI.
- Typosquatting at Scale: In 2024, security teams identified thousands of malicious packages targeting AI libraries. Names like openai-official, chatgpt-api, and tensorfllow (note the extra ‘l’) trapped thousands of developers.
- Data Poisoning: Recent Anthropic Research demonstrated how attackers could compromise ML models at training time, inserting backdoors that activate on specific inputs. Imagine your fraud detection AI suddenly ignoring transactions from specific accounts.
- Automated Social Engineering: Phishing isn’t just for emails anymore. AI systems are generating context-aware pull requests, comments, and even documentation that appears more legitimate than many genuine contributions.
A New Framework for Defense
Forward-thinking organizations are already adapting, and the results are promising.
The new defensive playbook includes:
- AI-Specific Detection: Google’s OSS-Fuzz project now includes statistical analysis that identifies code patterns typical of AI generation. Early results show promise in distinguishing AI-generated from human-written code – not perfect, but a solid first line of defense.
- Behavioral Provenance Analysis: Think of this as a polygraph for code. By tracking commit patterns, timing, and linguistic analysis of comments and documentation, systems can flag suspicious contributions.
- Fighting Fire with Fire: Microsoft’s Counterfit and Google’s AI Red Team are using defensive AI to identify threats. These systems can identify AI-generated malware variants that evade traditional tools.
- Zero-Trust Runtime Defense: Assume you’re already breached. Companies like Netflix have pioneered runtime application self-protection (RASP) that contains threats even after they execute. It’s like having a security guard inside every application.
- Human Verification: The “proof of humanity” movement is gaining traction. GitHub’s push for GPG-signed commits adds friction but dramatically raises the bar for attackers.
The Regulatory Imperative
If the technical challenges don’t motivate you, perhaps the regulatory hammer will. The EU AI Act isn’t messing around, and neither are your potential litigators.
The Act explicitly addresses AI supply chain security with comprehensive requirements, including:
- Transparency obligations: Document your AI usage and supply chain controls
- Risk assessments: Regular evaluation of AI-related threats
- Incident disclosure: 72-hour notification for AI-involved breaches
- Strict liability: You’re responsible even if “the AI did it”
Penalties scale with your global revenue, up to €35 million or 7% of worldwide turnover for the most serious violations. For context, that would be a substantial penalty for a large tech company.
But here’s the silver lining: the same controls that protect against AI attacks typically satisfy most compliance requirements.
Your Action Plan Starts Now
The convergence of AI and supply chain attacks isn’t some distant threat – it’s today’s reality. But unlike many cybersecurity challenges, this one comes with a roadmap.
Immediate Actions (This Week):
- Audit your dependencies for typosquatting variants.
- Enable commit signing for critical repositories.
- Review packages added in the last 90 days.
Short-term (Next Month):
- Deploy behavioral analysis in your CI/CD pipeline.
- Implement runtime protection for critical applications.
- Establish “proof of humanity” for new contributors.
Long-term (Next Quarter):
- Integrate AI-specific detection tools.
- Develop an AI incident response playbook.
- Align with regulatory requirements.
The organizations that adapt now won’t just survive, they’ll have a competitive advantage. While others scramble to respond to breaches, you’ll be preventing them.
For the full action plan and recommended vendors, download the CISO’s guide PDF here.
Source: thehackernews.com…