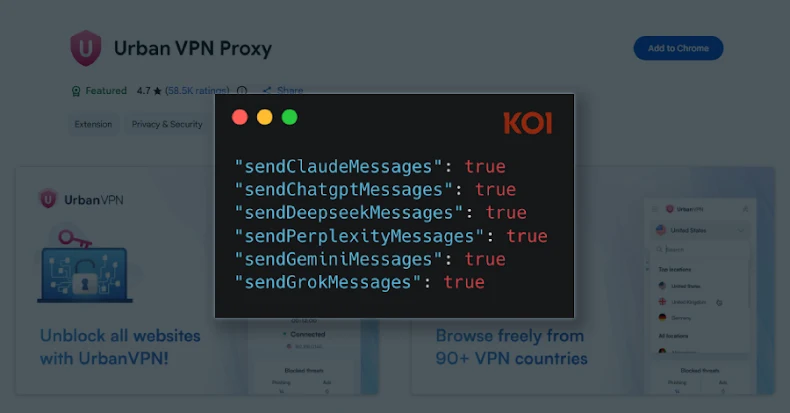
A Google Chrome extension with a “Featured” badge and six million users has been observed silently gathering every prompt entered by users into artificial intelligence (AI)-powered chatbots like OpenAI ChatGPT, Anthropic Claude, Microsoft Copilot, DeepSeek, Google Gemini, xAI Grok, Meta AI, and Perplexity.
The extension in question is Urban VPN Proxy, which has a 4.7 rating on the Google Chrome Web Store. It’s advertised as the “best secured Free VPN access to any website, and unblock content.” Its developer is a Delaware-based company named Urban Cyber Security Inc. On the Microsoft Edge Add-ons marketplace, it has 1.3 million installations.
Despite claiming that it allows users to “protect your online identity, stay protected, and hide your IP,” the extension was updated on July 9, 2025, when version 5.5.0 was released with the AI data harvesting enabled by default using hard-coded settings.
Specifically, this is achieved by means of a tailored executor JavaScript that’s triggered for each of the AI chatbots (i.e., chatgpt.js, claude.js, gemini.js) to intercept and gather the conversations every time a user who has installed the extension visits any of the targeted platforms.
Once the script is injected, it overrides the browser APIs used to handle network requests – fetch() and XMLHttpRequest() – to make sure that every request is first routed through the extension’s code so as to capture the conversation data, including users’ prompts and the chatbot’s responses, and exfiltrate them to two remote servers (“analytics.urban-vpn[.]com” and “stats.urban-vpn[.]com”).
The exact list of data captured by the extension is as follows –
- Prompts entered by the user
- Chatbot responses
- Conversation identifiers and timestamps
- Session metadata
- AI platform and model used
“Chrome and Edge extensions auto-update by default,” Koi Security’s Idan Dardikman said in a report published today. “Users who installed Urban VPN for its stated purpose – VPN functionality – woke up one day with new code silently harvesting their AI conversations.”
It’s worth mentioning that Urban VPN’s updated privacy policy, as of June 25, 2025, mentions that it collects this data to enhance Safe Browsing and for marketing analytics purposes, and that any other secondary use of the gathered AI prompts will be carried out on de-identified and anonymized data –
As part of the Browsing Data, we will collect the prompts and outputs quired [sic] by the End-User or generated by the AI chat provider, as applicable. Meaning, we are only interested in the AI prompt and the results of your interaction with the chat AI.
Due to the nature of the data involved in AI prompts, some sensitive personal information may be processed. However, the purpose of this processing is not to collect personal or identifiable data, we cannot fully guarantee the removal of all sensitive or personal information, we implement measures to filter out or eliminate any identifiers or personal data you may submit through the prompts and to de-identify and aggregate the data.
One of the third-parties it shares “Web Browsing Data” with is an affiliated ad intelligence and brand monitoring firm named BIScience. The company uses the raw (not anonymized) data to create insights that are “commercially used and shared with Business Partners,” the VPN software maker notes.
It’s worth noting BiScience, which also happens to own Urban Cyber Security Inc., was called out by an anonymous researcher earlier this January for collecting users’ browsing history, or clickstream data, as it’s called, under misleading privacy policy disclosures.
The company is alleged to provide a software development kit (SDK) to partner third-party extension developers to collect clickstream data from users, which is transmitted to the sclpfybn[.]com and other endpoints under its control.
“BIScience and partners take advantage of loopholes in the Chrome Web Store policies, mainly exceptions listed in the Limited Use policy, which are the ‘approved use cases,’” the researcher noted, adding they “develop user-facing features that allegedly require access to browsing history, to claim the ‘necessary to providing or improving your single purpose’ exception.”
On the extension listing page, Urban VPN also highlights an “AI protection” feature, which it says checks prompts for personal data, chatbot responses for suspicious or unsafe links, and displays a warning before users submit their prompts or click on them.
While this monitoring is framed as preventing users from accidentally sharing any personal information, what the developers fail to mention is that the data collection happens regardless of whether the feature is enabled.
“The protection feature shows occasional warnings about sharing sensitive data with AI companies,” Dardikman said. “The harvesting feature sends that exact sensitive data – and everything else – to Urban VPN’s own servers, where it’s sold to advertisers. The extension warns you about sharing your email with ChatGPT while simultaneously exfiltrating your entire conversation to a data broker.”
Koi Security said it observed identical AI harvesting functionality in three other unique extensions from the same publisher across Chrome and Microsoft Edge, taking its total install base to over eight million –
- 1ClickVPN Proxy
- Urban Browser Guard
- Urban Ad Blocker
All these extensions, with the exception of Urban Ad Blocker for Edge, carry the “Featured” badge, giving users an impression that they follow the platform’s “best practices and meet a high standard of user experience and design.”
“These badges signal to users that the extensions have been reviewed and meet platform quality standards,” Dardikman pointed out. “For many users, a Featured badge is the difference between installing an extension and passing it by – it’s an implicit endorsement from Google and Microsoft.”
The findings once again demonstrate how trust associated with extension marketplaces can be abused to amass sensitive data at scale, especially at a time when users are increasingly sharing deeply personal information, getting advice, and discussing emotions with AI chatbots.
The Hacker News has reached out to both Google and Microsoft for comment, and we will update the story if we hear back.
Source: thehackernews.com…