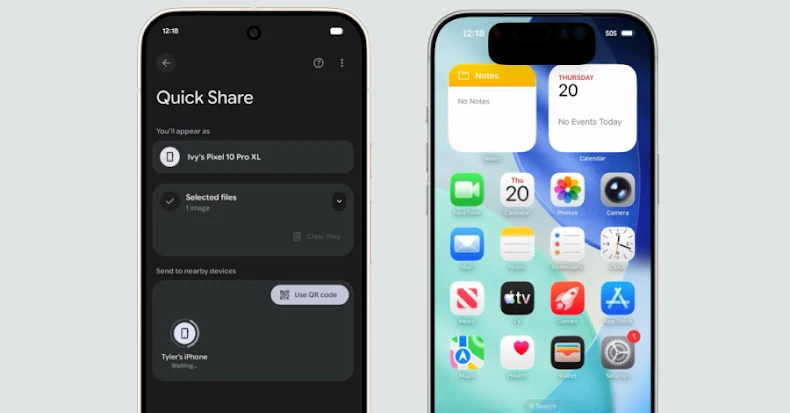
The Latest
-
Google Brings AirDrop Compatibility to Android’s Quick Share Using Rust-Hardened Security
-
APT24 Deploys BADAUDIO in Years-Long Espionage Hitting Taiwan and 1,000+ Domains
-
Why IT Admins Choose Samsung for Mobile Security
-
SEC Drops SolarWinds Case After Years of High-Stakes Cybersecurity Scrutiny