The Latest
-
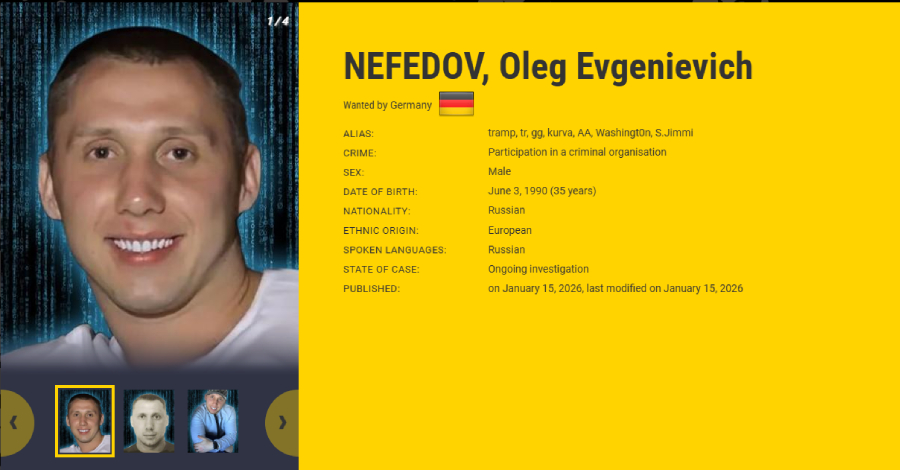
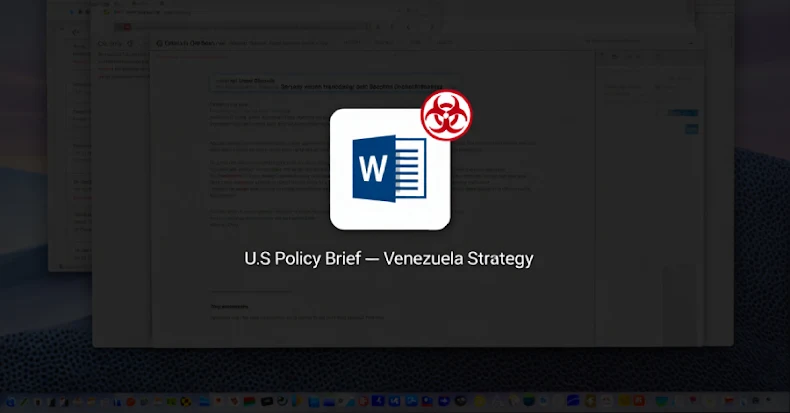
LOTUSLITE Backdoor Targets U.S. Policy Entities Using Venezuela-Themed Spear Phishing
-
Your Digital Footprint Can Lead Right to Your Front Door
-
Model Security Is the Wrong Frame – The Real Risk Is Workflow Security
-
ThreatsDay Bulletin: AI Voice Cloning Exploit, Wi-Fi Kill Switch, PLC Vulns, and 14 More Stories