The Latest
-
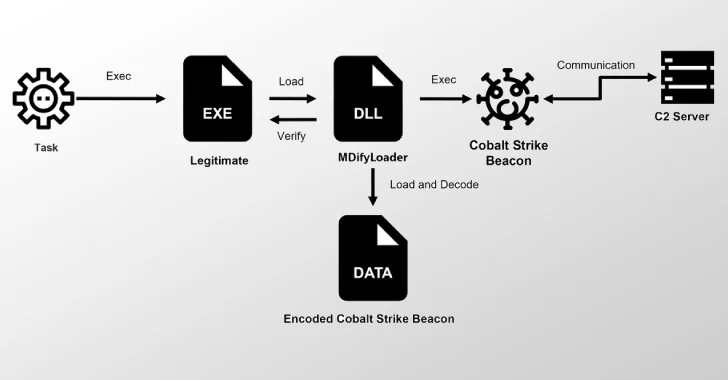
Ivanti Zero-Days Exploited to Drop MDifyLoader and Launch In-Memory Cobalt Strike Attacks
-
UNG0002 Group Hits China, Hong Kong, Pakistan Using LNK Files and RATs in Twin Campaigns
-
China's Massistant Tool Secretly Extracts SMS, GPS Data, and Images From Confiscated Phones
-
CERT-UA Discovers LAMEHUG Malware Linked to APT28, Using LLM for Phishing Campaign