The Latest
-
China's Massistant Tool Secretly Extracts SMS, GPS Data, and Images From Confiscated Phones
-
CERT-UA Discovers LAMEHUG Malware Linked to APT28, Using LLM for Phishing Campaign
-
From Backup to Cyber Resilience: Why IT Leaders Must Rethink Backup in the Age of Ransomware
-
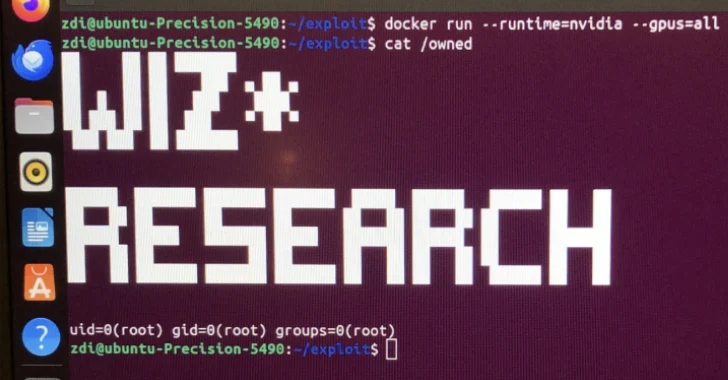
Critical NVIDIA Container Toolkit Flaw Allows Privilege Escalation on AI Cloud Services