The Latest
-
Application Containment: How to Use Ringfencing to Prevent the Weaponization of Trusted Software
-
ServiceNow AI Agents Can Be Tricked Into Acting Against Each Other via Second-Order Prompts
-
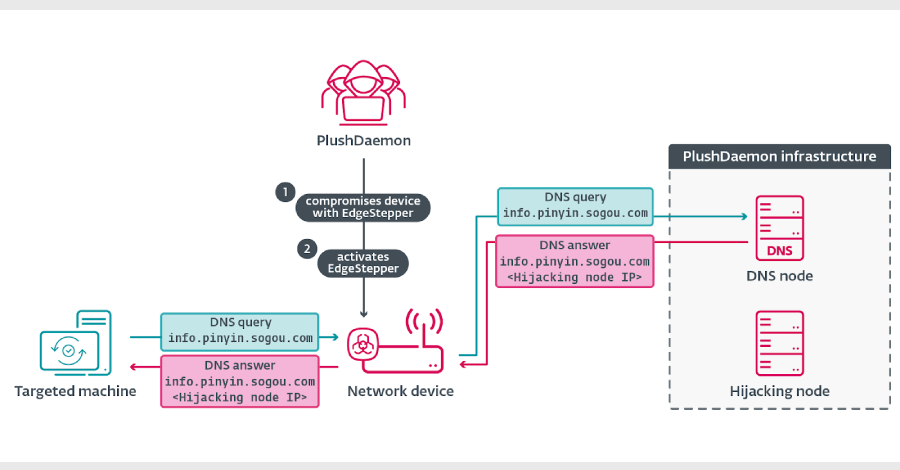
EdgeStepper Implant Reroutes DNS Queries to Deploy Malware via Hijacked Software Updates
-
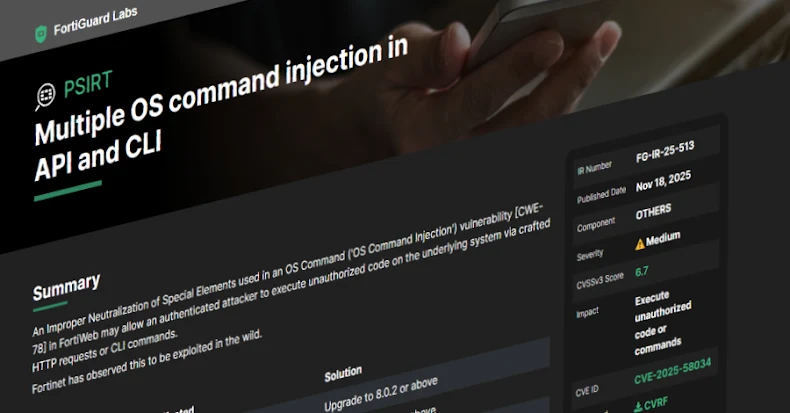
Fortinet Warns of New FortiWeb CVE-2025-58034 Vulnerability Exploited in the Wild