The Latest
-
The Hidden Risks of SaaS: Why Built-In Protections Aren't Enough for Modern Data Resilience
-
Iranian APT35 Hackers Targeting Israeli Tech Experts with AI-Powered Phishing Attacks
-
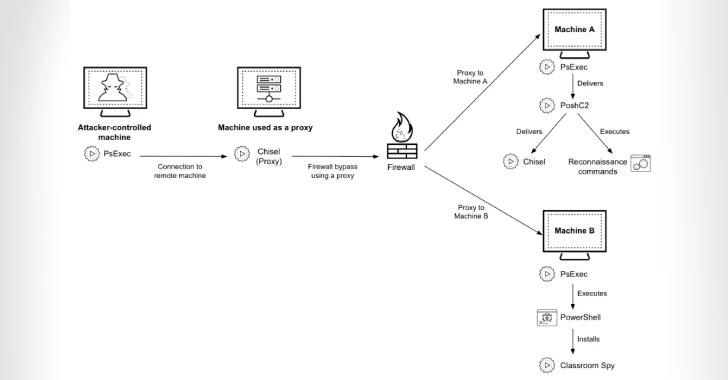
Cyber Criminals Exploit Open-Source Tools to Compromise Financial Institutions Across Africa
-
CISA Adds 3 Flaws to KEV Catalog, Impacting AMI MegaRAC, D-Link, Fortinet