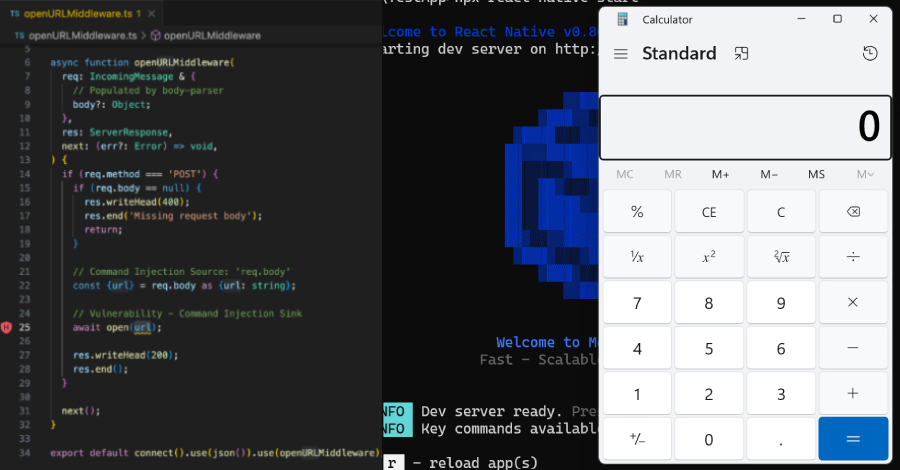
Raise your hand if you’ve heard the myth, “Android isn’t secure.”
Android phones, such as the Samsung Galaxy, unlock new ways of working. But, as an IT admin, you may worry about the security—after all, work data is critical.
However, outdated concerns can hold your business back from unlocking its full potential. The truth is, with work happening everywhere, every device connected to your network is a potential security breach point. As threats evolve, so must the tools to defend against them.
Allow me to introduce Samsung Knox—a built-in security platform that combines hardware and software protections on Samsung Galaxy devices. It’s loaded with features and is designed to safeguard data, provide IT teams with deeper control, and offer a flexible foundation for enterprise needs.
Let’s take a look at some myths about open source and how Samsung can get you on the right path to success.
Myth 1: “Isn’t Android more prone to malware and attacks?”
Common concerns around sideloading and third-party apps can be addressed through Samsung Knox’s enterprise controls, which let IT admins curate approved apps and prevent sideloading. Plus, AI-powered malware defense adds another layer of protection to help keep the Android ecosystem secure. Here’s how:
Proactive protection at scale:
- Google Play Protect scans over 200 billion apps daily, ensuring threats are blocked before they spread.
- According to Google, Managed Google Play devices see an exceptionally low rate of potentially harmful app installs, even when company-published apps are included.
Extra defense with Samsung Knox on Samsung Galaxy devices:
- Samsung Message Guard protects Samsung Galaxy devices from zero-click attacks by automatically isolating and scanning suspicious image files received through messaging apps.
- DEFEX (Defeat Exploit) detects abnormal app behaviours and can terminate them before they become active threats.
Key point: Android security isn’t about being open or closed—it’s about layered, proactive protection. With Samsung Knox on Samsung Galaxy devices, enterprises get exactly that.
Myth 2: “Aren’t modern threats about platforms, not people?”
A growing number of breaches today actually stem from human vulnerabilities—not just the platform itself! Let’s take a look:
The bottom line is, the biggest risks originate from overlooked basics. For example, failing to update devices with the latest security patches and not implementing the necessary IT policies—this applies to both open and closed platforms!
Here’s how Samsung Knox helps:
- Know which device to update, when, and why: Knox Asset Intelligence provides IT admins centralized visibility into such information, and Knox E-FOTA provides precise and stable version control that’s hard to match on other platforms.
- Manage work devices and data according to your business needs: Samsung Knox enhances the security of Samsung Galaxy devices by providing granular security controls and comprehensive visibility. Users can access these features in multiple ways, including connecting to their own Enterprise Mobility Management systems, using Knox Suite.
Key point: Closed systems don’t automatically protect against human error. Enterprises need a layered defense, strong policies, and visibility into device behavior. That’s exactly what Samsung Knox delivers!
Myth 3: “Android updates are slower and harder to manage, right?”
With modern Android and Samsung Knox tools, updates are now faster, more flexible, and fully manageable at scale. Let’s take a look:
Android innovations:
- Mainline enables critical security and system updates to be pushed directly through Google Play—no wait required for OS upgrades.
Samsung innovations:
The Samsung Knox platform on Samsung Galaxy devices enables hard-to-beat detailed scheduling and stable deployment. Using Knox E-FOTA, IT admins can access:
- Target specific firmware versions instead of just the latest release.
- Block all types of user updates, including over-the-air, USB, and unauthorized installations to unintended versions.
- Schedule updates based not only on time but also on factors like battery level and network bandwidth.
- Perform on-prem firmware updates without relying on a cloud network environment.
Key point: With Knox E-FOTA, you gain a strategic level of control that turns mobile updates from a support burden into a predictable, business-aligned process!
The reality: Samsung Knox transforms Android security
Samsung Galaxy devices, secured by Samsung Knox, are redefining what mobile security looks like for enterprises. By addressing old vulnerabilities, tackling human-driven threats, and giving IT strategic update control, Samsung Knox shifts Android from “perceived risk” to enterprise-grade resilience.
The result? Government-grade protection, centralized visibility, and smarter management. Don’t take my word for it; find out for yourself by trying Samsung Knox.
Source: thehackernews.com…