Running a SOC often feels like drowning in alerts. Every morning, dashboards light up with thousands of signals; some urgent, many irrelevant. The job is to find the real threats fast enough to keep cases from piling up, prevent analyst burnout, and maintain client or leadership confidence.
The toughest challenges, however, aren’t the alerts that can be dismissed quickly, but the ones that hide in plain sight. These tricky threats drag out investigations, create unnecessary escalations, and quietly drain resources over time.
Why Detection Gaps Keep Opening
What slows SOCs down isn’t the flood of alerts alone but the way investigations get split across disconnected tools. Intel in one platform, detonation in another, enrichment in a third; every switch wastes time. Across hundreds of cases, those minutes add up to stalled investigations, unnecessary escalations, and threats that linger longer than they should.
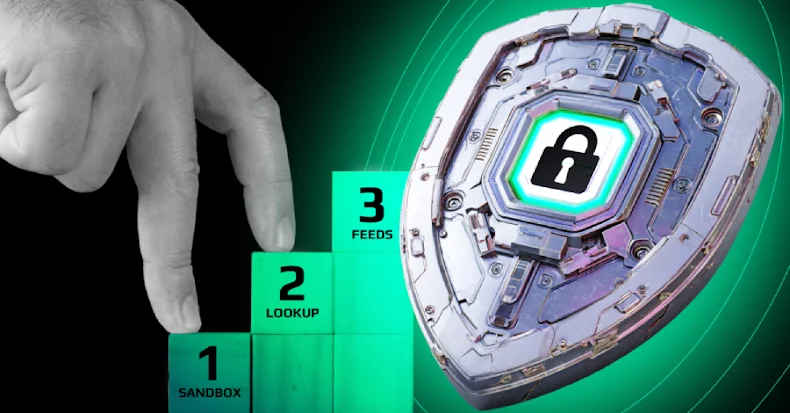
Action Plan That Delivers 3× SOC Efficiency in Threat Detection
SOC teams looking to close detection gaps have found one approach that works: building detection as a continuous workflow, where every step reinforces the next. Instead of stalling in disconnected tools, analysts move through a process that flows, from filtering alerts to detonating suspicious files to validating indicators.
A recent ANY.RUN survey shows just how much this shift can change SOC performance:
- 95% of SOC teams reported faster investigations
- 94% of users said triage became quicker and clearer
- 21 minutes saved on MTTR for each case
- Up to 58% more threats identified overall
 |
| 3-step action plan with its impact when using ANY.RUN |
Behind these numbers is more than speed. SOCs that adopted this workflow reduced alert overload, gained clearer visibility into complex attacks, and built confidence in compliance and reporting. Teams also grew faster in expertise, as analysts learned by doing rather than relying solely on static reports.
So how are these numbers possible? The answer lies in three practical steps SOC teams have already put into action.
Let’s look at how this plan works, and how you can implement it in your own workflows.
Step 1: Expand Threat Coverage Early
The earlier a SOC can spot an incident, the faster it can respond. Threat Intelligence Feeds give analysts fresh, actionable IOCs drawn from the latest malware campaigns; IPs, domains, and hashes seen in real-world attacks. Instead of chasing alerts blindly, teams start with data that reflects what’s happening across the threat landscape right now.
 |
| TI Feeds as your first step in threat detection |
With this early coverage, SOCs gain three key advantages: they catch incidents sooner, stay aligned with current threats, and cut down on noise that clutters Tier 1. In practice, that means a 20% decrease in Tier 1 workload and fewer escalations eating into senior analysts’ time.
Don’t let detection gaps slow your team down. Start with the 3-level process today and give your SOC the clarity and speed it needs.
The best part is that Threat Intelligence Feeds are available in multiple formats with simple integration options, so they can plug directly into your existing SIEM, TIP, or SOAR setup without disrupting workflows.
By filtering out duplicates and irrelevant signals at the start, Threat Feeds free up resources and ensure analysts focus on the alerts that actually matter.
Step 2: Streamline Triage & Response with Interactive Sandbox
Once alerts are filtered, the next challenge is proving what’s left. An interactive sandbox becomes the SOC’s proving ground. Instead of waiting for static reports, analysts can detonate suspicious files and URLs in real time, watching behavior unfold step by step.
This approach exposes what most automated defenses miss; payloads that need clicks to activate, staged downloads that appear over time, and evasive tactics designed to fool passive detection.
 |
| ANY.RUN’s sandbox analyzing complex threat |
The result is faster, clearer answers:
- Evasive attacks exposed before they can escalate
- Actionable threat reports generated for quick response
- Routine tasks minimized with automated investigations
In practice, SOCs achieve a 15-second median detection time, turning what used to be long, uncertain investigations into rapid, decisive outcomes.
By combining real-time visibility with automation, the sandbox gives specialists of all levels the confidence to act quickly, while freeing senior staff from spending hours on routine triage.
Step 3: Strengthen Proactive Defense with Threat Intelligence Lookup
Even with full sandbox results, one question always remains: has this threat been seen before? Knowing whether an IOC is part of a fresh campaign or one already circulating across industries can completely change how a SOC responds.
That’s why the third step is implementing Threat Intelligence Lookup. By tapping into live attack data contributed by more than 15,000 SOCs worldwide, analysts instantly enrich their findings and connect isolated alerts to wider patterns.
 |
| TI Lookup search of attack and its relevant sandbox analyses |
The advantages are clear:
- Hidden threats uncovered through proactive hunting
- Greater incident clarity with rich historical context
- Real-time visibility into evolving campaigns
With access to 24× more IOCs than typical isolated sources, security professionals can validate faster, close tickets sooner, and anticipate what might be coming next.
This final step ensures that every investigation ends with stronger evidence; not just a snapshot of one case, but an understanding of how it fits into the bigger threat landscape.
Build a Stronger SOC With a Unified Detection Workflow
Closing detection gaps is possible by creating a workflow where every stage strengthens the next. With early filtering from Threat Feeds, real-time visibility from the sandbox, and global context from Lookup, SOCs move from fragmented detection to a continuous process that delivers measurable results: faster triage, fewer escalations, and up to 3× greater efficiency in threat detection.
Organizations worldwide are already seeing the benefits:
- 74% of Fortune 100 companies use ANY.RUN to reinforce SOC operations
- 15,000+ organizations have integrated it into their detection workflows
- 500,000+ users rely on it daily for malware analysis and threat intelligence
Boost your detection rate, cut investigation time, and strengthen SOC efficiency.
Connect with ANY.RUN’s experts to explore how this approach can work for your team.
Source: thehackernews.com…