A high-severity security flaw has been disclosed in the One Identity OneLogin Identity and Access Management (IAM) solution that, if successfully exploited, could expose sensitive OpenID Connect (OIDC) application client secrets under certain circumstances.
The vulnerability, tracked as CVE-2025-59363, has been assigned a CVSS score of 7.7 out of 10.0. It has been described as a case of incorrect resource transfer between spheres (CWE-669), which causes a program to cross security boundaries and obtain unauthorized access to confidential data or functions.
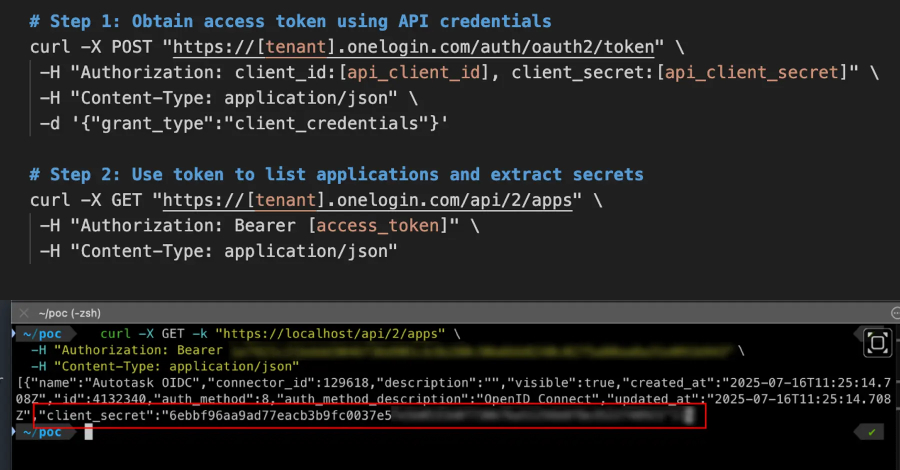
CVE-2025-59363 “allowed attackers with valid API credentials to enumerate and retrieve client secrets for all OIDC applications within an organization’s OneLogin tenant,” Clutch Security said in a report shared with The Hacker News.
The identity security said the problem stems from the fact that the application listing endpoint – /api/2/apps – was configured to return more data than expected, including the client_secret values in the API response alongside metadata related to the apps in a OneLogin account.
The steps to pull off the attack are listed below –
- Attacker uses valid OneLogin API credentials (client ID and secret) to authenticate
- Request access token
- Call the /api/2/apps endpoint to list all applications
- Parse the response to retrieve client secrets for all OIDC applications
- Use extracted client secrets to impersonate applications and access integrated services
Successful exploitation of the flaw could allow an attacker with valid OneLogin API credentials to retrieve client secrets for all OIDC applications configured within a OneLogin tenant. Armed with this access, the threat actor could leverage the exposed secret to impersonate users and gain access to other applications, offering opportunities for lateral movement.
OneLogin’s role-based access control (RBAC) grants API keys broad endpoint access, meaning the compromised credentials could be used to access sensitive endpoints across the entire platform. Compounding matters further is the lack of IP address allowlisting, as a result of which it’s possible for attackers to exploit the flaw from anywhere in the world, Clutch noted.
Following responsible disclosure on July 18, 2025, the vulnerability was addressed in OneLogin 2025.3.0, which was released last month by making OIDC client_secret values no longer visible. There is no evidence that the issue was ever exploited in the wild.
“Identity providers serve as the backbone of enterprise security architecture,” Clutch Security said. “Vulnerabilities in these systems can have cascading effects across entire technology stacks, making rigorous API security essential.”
Source: thehackernews.com…



Leave a Reply